As you already know BitLocker is a Microsoft solution for a drive encryption. BitLocker can be very useful when you have a lot of Remote users or users that are travel very often.
When you have encrypted the devices drives you don't need have to worry about the data in case of stolen or lost.
You can find various articles that i wrote regarding the BitLocker here.
I spent lot o hours in my Lab to understand how can successful deploy a BitLocker policy to the device. It wasn't an easy task. However i found the way and i would like to share it in this article..
Let's see one by one what do you need and how can use it.
Hardware Requirements
Before start with the implementation you must understand that BitLocker has some hardware requirements. These are:
-
For TPM 2.0 devices, you must have native Unified Extensible Firmware Interface (UEFI) configured. (Secure boot is not required but adds another layer of security.)
- BIOS or UEFI firmware must support USB mass storage.
- You must partition the hard disk into an operating system drive formatted with NTFS and a system drive with at least 350 MB formatted as FAT32 for UEFI and NTFS for BIOS.
How to apply BitLocker to the Devices
BitLocker in Intune can be applied with two different ways:
-
Endpoint security disk encryption policy for BitLocker
- Device configuration profile for endpoint protection for BitLocker
Let's start!!
How to create the Endpoint security policy for BitLocker
- Open the Microsoft Intune admin Center and select Endpoint Security -- Disk Encryption -- Create Policy

-
Select Windows 10 and Later and Template BitLocker and click Create.
-
Type the name of the Policy.
-
Configuration Settings include the followings:
-
BitLocker
-
Administrative Templates
-
-
The BitLocker has the following three settings. Based on your requirements you can configure it except the first option as described.
-
Require Drive encryption = It's recommended at least until now don't enable the Require Drive encryption because Microsoft confirms 65000 error when enable the option. The bug is related to BitLocker CSP encryption reporting.
-
Allow Warning For Other Disk Encryption
-
Configure Recovery Password Rotation
-

-
The Administrative Templates has the following options:
- BitLocker Drive encryption which related with the drive encryption method.
- BitLocker Drive encryption for the OS Drives
- BitLocker Drive encryption for the Fixed Driver
- BitLocker Drive encryption for the Removable Drives
-
Enable the following options at least to start the deployment of the Bitlocker in the Devices that you need.
-
In the Administrative Templates -- Windows Components -- BitLocker Drive encryption

- In the Administrative Templates -- Windows Components -- BitLocker Drive encryption -- Operating System Drives


- In the Administrative Templates -- Windows Components -- BitLocker Drive encryption -- Fixed Data Drives

- In the Administrative Templates -- Windows Components -- BitLocker Drive encryption -- Removable Data Drives

-
In the Scope Tags just click Next.

-
In the Assignments you must assign a Group with the Devices that you want to apply the BitLocker policy. Based on the configuration create the Group in your Active Directory if you have Hybrid AAD Join or in the Azure Active Directory if you are in the cloud. Click Next.

-
In the Review + Create click Create to proceed.

How to Monitoring if the Device is Encrypted or not, if has TPM or not
Sometimes we are looking various information depends in our deployments. One of this information is if the devices has TPM.
-
Open the Microsoft Intune Admin Center
-
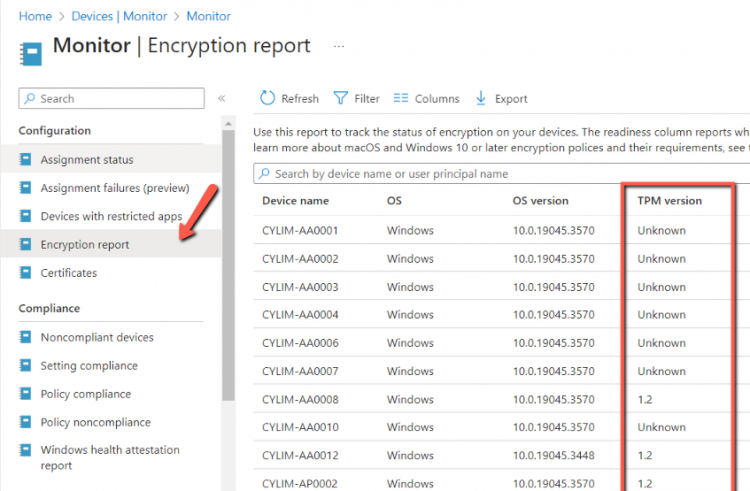
Click on Devices - - Monitor - - Encryption report.
-
This report can gives us the TPM availability and Disc encryption status for each device .
How to enable Silent BitLocker Encryption to to the Devices
Silent BitLocker encryption means that you can enable BitLocker encryption without presenting any UI to the user. The encryption will be started automatically when the Policy applied to the device.
We can use either the Endpoint Profile Encryption or Device Configuration Profile to enable the Silent BitLocker encryption.
Today i will explain how can configure the Device Configuration Profile and all the prerequisites.
Device Prerequisites
Before you will start enable the Silent BitLocker encryption you must met the followings based on Microsoft documentation
-
If end users sign in to the devices as Administrators, the device must run Windows 10 version 1803 or later, or Windows 11.
- If end users sign in to the devices as Standard Users, the device must run Windows 10 version 1809 or later, or Windows 11.
- The device must be Microsoft Entra joined or Microsoft Entra hybrid joined.
- Device must contain at least TPM (Trusted Platform Module) 1.2.
- The BIOS mode must be set to Native UEFI only.
Required settings for the Silent BitLocker encryption.
For better understanding let's see which extra settings must be enabled based on Microsoft documentation
Required Settings for the Endpoint security disk encryption policy
- Hide prompt about third-party encryption = Yes
- Allow standard users to enable encryption during Autopilot = Yes
- Require Key File Creation = Allowed or Blocked
- Recovery Password Creation = Allowed or Required
- Compatible TPM startup - Configure this as Allowed or Required
- Compatible TPM startup PIN - Configure this as Blocked
- Compatible TPM startup key - Configure this as Blocked
- Compatible TPM startup key and PIN - Configure this as Blocked
Required Settings for the Device Configuration Profile
- Encrypt Devices = Require
BitLocker base settings
- Warning for other disk encryption = Block.
- Allow standard users to enable encryption during Microsoft Entra join = Allow
BitLocker - OS Drive Settings
- User creation of recovery key = Allow or Do not allow 256-bit recovery key
- User creation of recovery password = Allow or Require 48-digit recovery password
- Compatible TPM startup - Configure this as Allow TPM or Require TPM
- Compatible TPM startup PIN - Configure this as Do not allow startup PIN with TPM
- Compatible TPM startup key - Configure this as Do not allow startup Key with TPM
- Compatible TPM startup key and PIN - Configure this as Do not allow startup Key and PIN with TPM
How to create the Device Configuration Profile to enable Silent BitLocker
Let's start to see the configuration in practice.
- From left menu in the Intune admin center click on Devices
- Click on Windows devices.
- Click on Configuration Profiles.
- Click Create --> New Policy.

- Select the followings
- Platform: Windows 10 and later.
- Profile type: Templates.
- Template name: Endpoint Protection.

- In the Basics type a name for the Configuration Profile and click Next.

- In the Configuration Settings expand the Windows Encryption.
- Change the Configuration based on the above paragraph Required settings for the Silent BitLocker encryption. Click Next.


- Assign a group that you should apply the Configuration Profile and click Next. Remember that can apply only in Groups and not in individual devices. So you must create a Group in the Active Directory with all the devices that you want to encrypted.

- In the Applicability Rules don't change anything and click Next.

- Review your settings and click Create.
Now that you have created the Device Configuration Policy, wait until the Policy will be applied to the Device.
Then verify in the Device that the the OS Dick encrypted.
If you want to force manual the Intune Policy to the device you can do it from the Windows 10 or 11 machine.
- Click Start and go to the Settings.
- Select the Accounts.
- Click on Access work or school.
- Click on the connected account and select Info.

- Scroll down and Click on button Sync.

How to verify that the BitLocker Policy applied to the Device
When you will deploy a BitLocker Policy, you need to monitoring the deployment status.
Fortunate you have a lot of ways to do that.
How to check the status from the Intune Admin Center
-
From the left menu click on the Endpoint Security.
-
Click on the Disk encryption
-
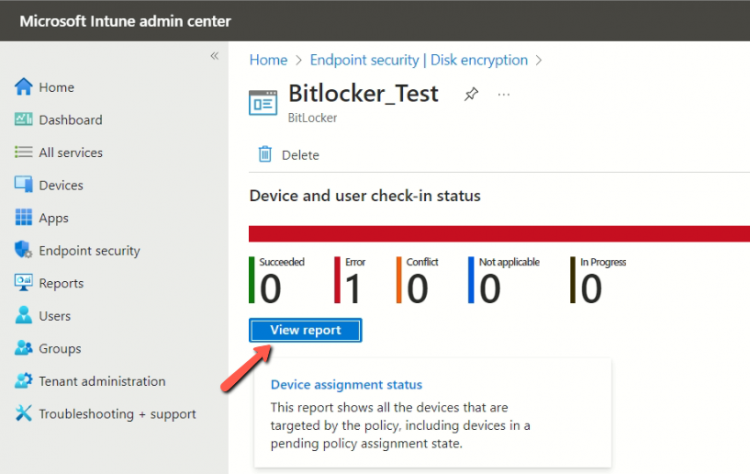
Select the Policy that you have deployed, and you will see the status.
-
For more details you can click on View report.
-
Click on the Device name.

- Now you can see a detail settings status of the device.

If the setting status Succeeded then the Device has received the BitLocker Policy. However, we aren't sure if the Deployment have been stopped due to any errors to the device.
How to check the status from the Windows Device
Sometimes you will not have all the details that you need to troubleshoot the errors that you will get.
However, you will face scenarios that the the Policy will have deployed successful but the BitLocker will not be started because of an errors.
These errors can't see it from the Intune Admin Center, but only from the Windows Device.
So let's see how can find out the errors.
In my scenario i had deploy successful the Configuration Profile. but the BitLocker failed to start. In the beginning i didn't know from where to start.
I didn't understand why the Disk wasn't encrypted but the Policy have been deployed successfully.
- So i started to search in the Windows Event Logs.
- The status of the BitLocker encryption you can find in from the Event Logs in Application and Services Logs - - Microsoft - - Windows - - BitLocker-API - - Management
- The encryption wasn't started because was prevented from backing up the recovery password to the Active Directory.

- To be honest i don't have seen any requirement in the Microsoft Documentation regarding the backup of recovery keys to Active Directory. However, it seems that we should be enable to back up the recovery keys to the Active Directory in the Device Configuration Policy.
- So i went to the Intune Admin Center
- Click On the Devices from the left menu
- Click on Windows
- Click on Configuration Profiles
- I selected the Silent_BitLocker Profile. It's the Profile that we are created earlier.
- I scrolled down to the Configuration settings and I edited.
- Expanded the Windows Encryption
- In the BitLocker OS-drive Settings i changed the following settings
- Save BitLocker recovery information to Microsoft Entra ID = Enable
- BitLocker recovery Information stored to Microsoft Entra ID = Backup recovery passwords and key packages
- Store recovery information in Microsoft Entra ID before enabling BitLocker = Require

- Then i forced the sync manually and the encryption started successfully.

- After sometime the OS disk was encrypted

To be honest it's not so easy the configuration from both side(Intune and Device), but it worth the time if you have lot of the Devices out of your Local network.
Because you will do it only once instead to run multiple steps until encrypt your disk for every new Device.
I hope to find valuable and helpful the article
Have a nice weekend !!!!





